Netcraft has recently observed that criminals abused SendGrid’s services to launch a phishing campaign impersonating SendGrid itself. The well-known provider, now owned by Twillio, makes sending emails at scale simple and flexible. In addition to scale, the promise of high deliverability and feature-rich tools make Sendgrid a sought-after service for legitimate businesses and a likely target for criminals.
The campaign observed uses a variety of complex lures, such as claiming the victim’s account has been suspended while its sending practices are reviewed or that the victim’s account is marked for removal due to a recent payment failure, combined with other SendGrid features to mask the actual destination of any malicious links.
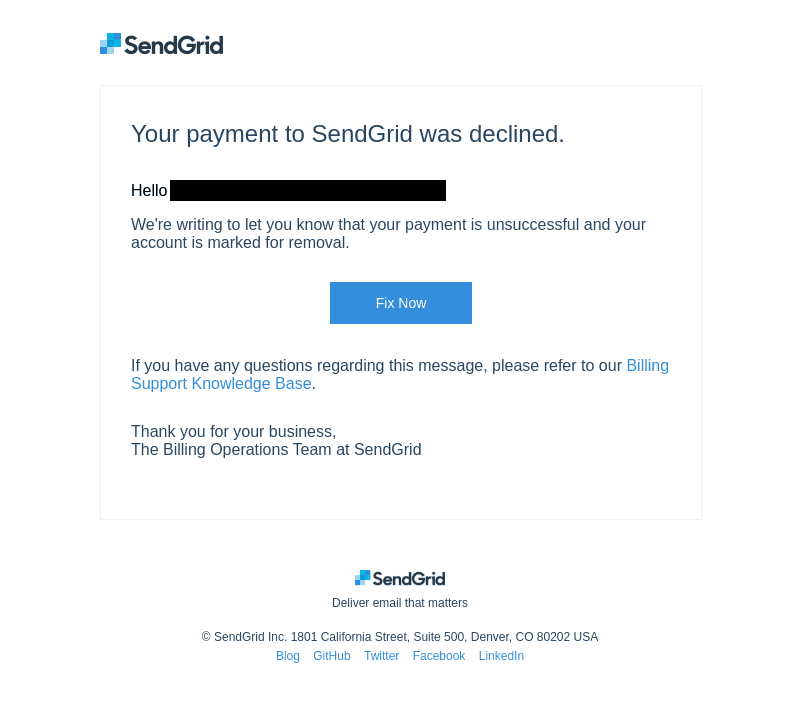
Screenshot of one of the phishing emails seen by Netcraft in the campaign.
The criminals behind the campaign used SendGrid’s click-tracking feature, with the malicious link masked behind a tracking link hosted by SendGrid. As the actual destination link is encoded in a URL parameter, even technically savvy recipients cannot determine its destination without following it.
https://u684436[.]ct[.]sendgrid.net/ls/click?upn=MlKqR181cN-2FwVofVyYroZohPHYCFmcOANwhWCUdTCBwPOc8txaiCuzTlogC05KN3LNFQ-2BuY0GGAqsU1nral07J5ZAzdZaZBAuJ7sV0-2BXHfumQD5I7-2FksS6M-2Bkp-2BkG47JcUbzDR8JwfwRM53-2BjxY8Q39KSfdEFQ9435uyTBM5TtspkyY3jUnvibv5C-2BopzMIluG2QhFh3lCZT2E5thEQQlvnZzjigw0zd2QIpDJ1mDMyGAOP9FKPeH-2BubdRj8uMW7TYzi-2FryttpaWt-2FacBOIgmTucX37Bpzwo8hDwYWOfxtiszu0DQpSrDO3oXpdkl-2B4s7wZAW0B-2FGDFBUzYJTXj74HRI9K2dpGobo82sm-2BazB2pF4rB-2BmwcxWwFL-2FpuLyZHB39O28qMVDOVLLbjWvpdUCCWXeMbVjwqJJJ-2FJJcfiX9cVoMVr52N2vZshdxGLBhIHeg5gMDA8qUev9sXguFrcp8VNlV-2FhMxARF1RUvbSCJCUd-2Faf2xJXq65WP0ikjyx7BLg1hmUr3QcV9IstauGE08g-3D-3DmcLN_IrVKFt61B0RSPoIcLeWyNg52nFk05lKq9QPi-2FlqEDp6KgcjnqupRcHzKcBBn7PVo8-2BxeSCeDL5jOu-2Bx5wws5UKOwmCQCTy6wc-2FTAihp-2FZilUgXpstXJftrsxyCzWfWHkMtlCi92uoep-2BB-2BEJJpbK-2BlDe4wqa-2FR0sOOAlwWz6aTEHqnEACadwVCrFtoPCBG68mO0yF5ItaBS0v1i7sukWtkhsoqWJbxt7FUowSScDsyM-3DExamining the email h
[…]
Content was cut in order to protect the source.Please visit the source for the rest of the article.
Read the original article: